Active Directory as a C2 Really ? I was amazed when i read a blog post on AD as a C2 on @Harmj0y‘s blog. Curiosity grew into me and wanted to explore it in my lab setup.
Why AD as a C2?
- Active Directory is a Central Authentication and Access control.
- All the Endpoints Workstations/Servers are connected to Active Directory.
- It solves Network segmentation Issues.
- Bypasses Internal Firewalls.
- No traffic sent to the target.
By default all the authenticated users have write access to some of their own user attributes and read access to other user’s attributes in active directory. User attributes with Read/Write access can be abused to store the payload and can turn an active directory into command & control. Powerview can be used to get users object access rights. @Harmj0y has created a POC Powershell script which abuses ‘msmqsigncertificates’ property to write payload in the user attribute.
The Powershell script will store the payload in ‘msmqsigncertificates’ which is an optional user property in Active Directory. The advantage of using ‘msmqsigncertificates’ is that it has 1MB of upper size limit and also has ‘partial attribute set’ with default schema. The payloads stored in ‘msmqsigncertificates‘ will be propagated to all copies of the global catalog in the forest due to partial attribute set to true.
So Basically one user changes their property field while other user continually query for world-readable information then report the results back to their own ‘msmqsigncertificates’. So That’s a 1MB two-way data channel.
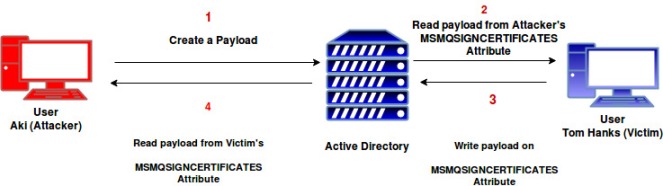
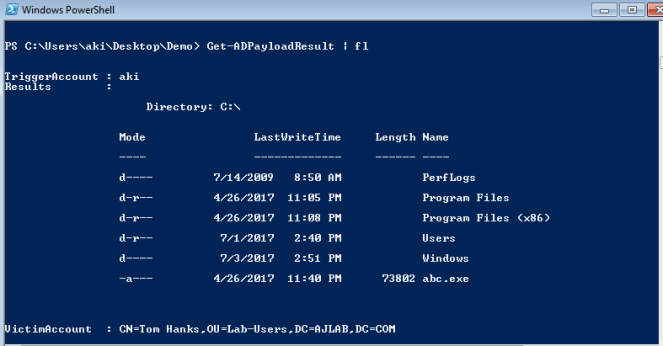
In our AD C2 scenario Aki (Attacker) will create a payload using the cmdlet ‘New-ADPayload‘. The payload will be compressed using .NET [IO.Compression.DeflateStream] compression and then Base64’ed data will be stored in the ‘msmqsigncertificates‘ attribute. This will also create a triggering Powershell script which needs to be run on the Victim (Tom Hanks) machine.

The triggering script needs to be executed on the victim machine and after running the script in victim machine, we will come back to attacker machine and use cmdlet ‘Get-ADPayloadResult’ to get the results.
Detection:
- Monitor Regular changes of Personal Information attribute.
- Lock down user’s permission to update Personal Information attribute.
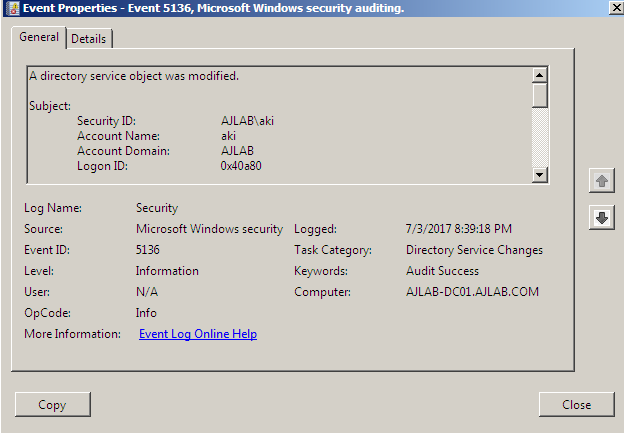
- Audit logs for Directory Service object modified and look out for windows Event ID 5136.
I have also created a video demo for AD C2
References:
https://msdn.microsoft.com/en-us/library/ms684394%28v=vs.85%29.aspx
http://www.harmj0y.net/blog/powershell/command-and-control-using-active-directory/
Click to access us-17-Miller-The-Active-Directory-Botnet.pdf